Fast ⚡ | Flexible 🔁 | Scalable 📈 | Secure 🔐 | Available 24/7 🕒 Email
If you suspect hidden surveillance, EMF exposure, or targeted spy harassment, contact Cyber Privilege for a forensic EMF investigation contact 8977308555
1. Introduction & Positioning
At Cyber Privilege, our mission is not just detection — it’s scientific investigation, bespoke mitigation, and legal-grade remedy. Our R&D unit continuously develops, tests, and refines methods to detect hidden RF/EMF harassment, spying attacks, and abnormal exposures that conventional vendors or consumer devices miss. We serve clients who are often dismissed by others: professionals, homemakers, students, farmers, business executives — all victims of stealth attacks.
We stand apart because:
We combine electromagnetic engineering + digital forensics + medical liaison in our framework.
Every case delivers a forensic report (raw logs, frequency heatmaps, temporal graphs) suitable for court, doctors, or regulatory agencies.
We calibrate instruments regularly, maintain ISO/compliance-level chains of custody, and defend our reports under scrutiny.
We help clients transition from victimhood to recovery and protection.
2. EMF / RF Damage: The Science & Evidence Base
What Are EMFs / EM Radiation?
Electromagnetic fields (EMFs) span a wide spectrum — from extremely low frequencies (power lines) to radio frequencies (mobile, Wi-Fi) to microwaves, infrared, visible light, ultraviolet and beyond.
Electric fields result from voltage differences (even when no current flows).
Magnetic fields result from electric current flow.
When combined and oscillating, they form electromagnetic waves, characterized by frequency (f) and wavelength (λ), related by c=λ⋅fc = λ \cdot fc=λ⋅f (where ccc is speed of light).
Different frequencies interact differently with biological tissues.
A typical EM spectrum diagram (radio wave → microwave → infrared → visible → ultraviolet) helps situate where RF/EMF from phones & routers lie.
Sources — Natural vs Man-Made
Natural sources:
Earth’s magnetic field
Atmospheric phenomena (lightning, charge build-up)
Human-made sources:
Power lines, household wiring, transformers
Mobile towers / base stations
Wi-Fi routers, smartphones, tablets
Microwave ovens, radars, broadcast transmitters
IoT devices, RFID, Bluetooth
These sources collectively form a background field environment; intermittent or high-level anomalies may signal harassment / misuse.
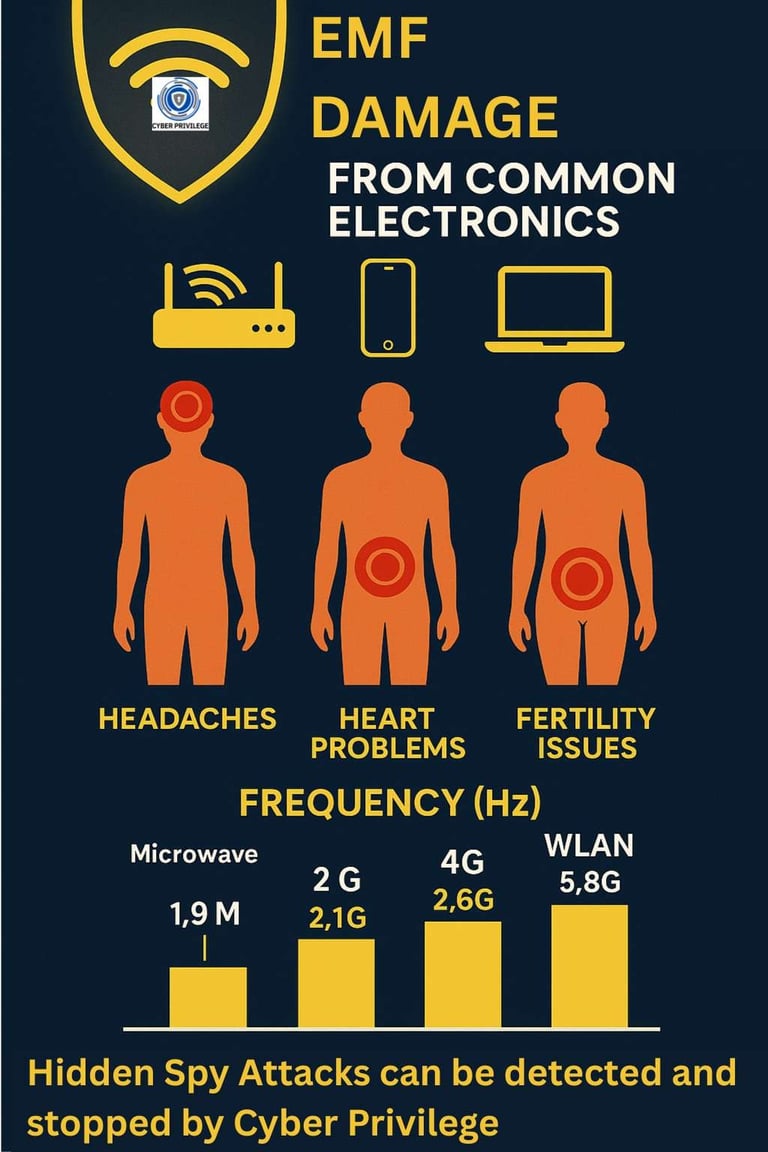
Biological Effects & Risks (Current Research)
Note: It’s critical to present this carefully — we don’t overpromise cures, but emphasize why monitoring is needed:
Heating (thermal effects): The primary accepted mechanism. At high enough power densities, tissues absorb energy and warm. Regulations are built to prevent dangerous heating in tissues.
Low-level exposures: The evidence is mixed. Some studies report non-thermal effects (oxidative stress, subtle neuro changes), but these remain areas of active research.
Induced currents / nerve stimulation: At very low frequencies, magnetic fields can induce small currents in the body. If these approach biological thresholds, stimulation of nerves/muscles may occur.
Electromagnetic hypersensitivity (EHS): Some individuals report symptoms (headache, fatigue, dizziness) they attribute to low-level EMF exposure. However, double-blind studies have had mixed or inconclusive results, so the mechanism or causality remains debated in the scientific community.
The World Health Organization (WHO) and various international bodies continue to monitor research and update guidelines — so our R&D efforts remain cutting-edge.
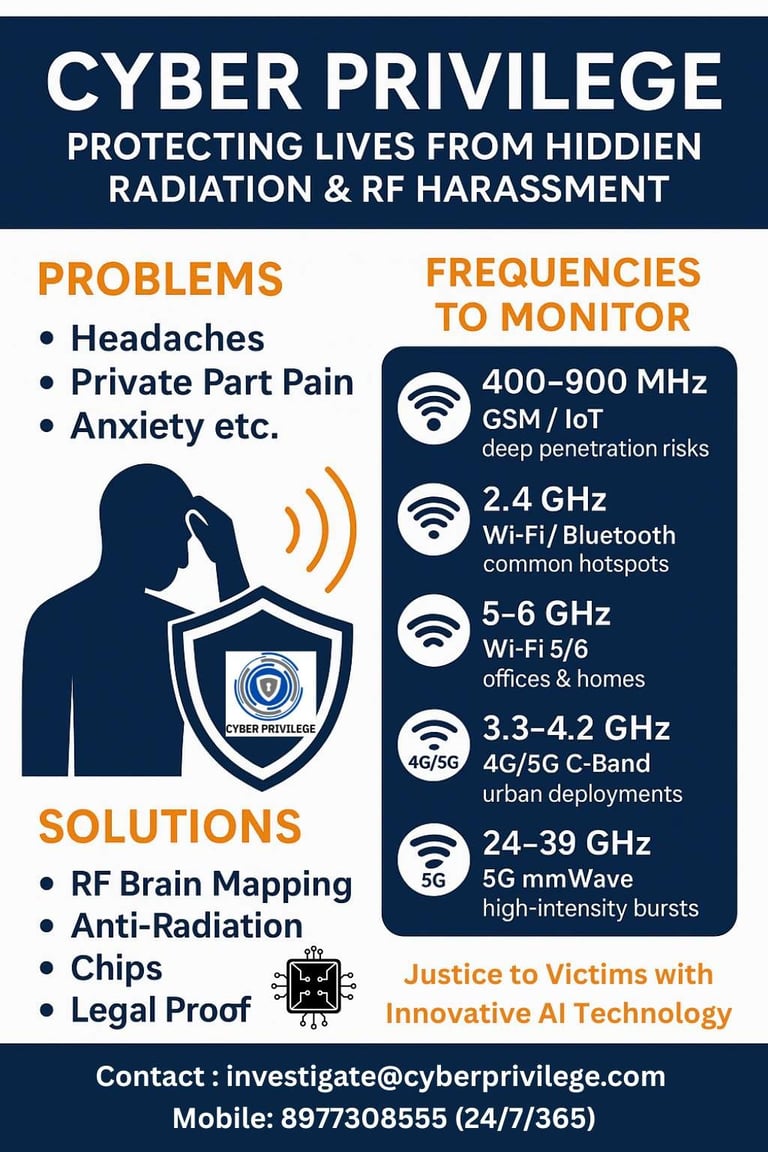
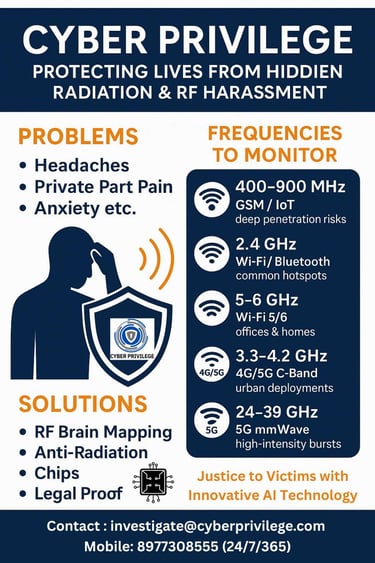
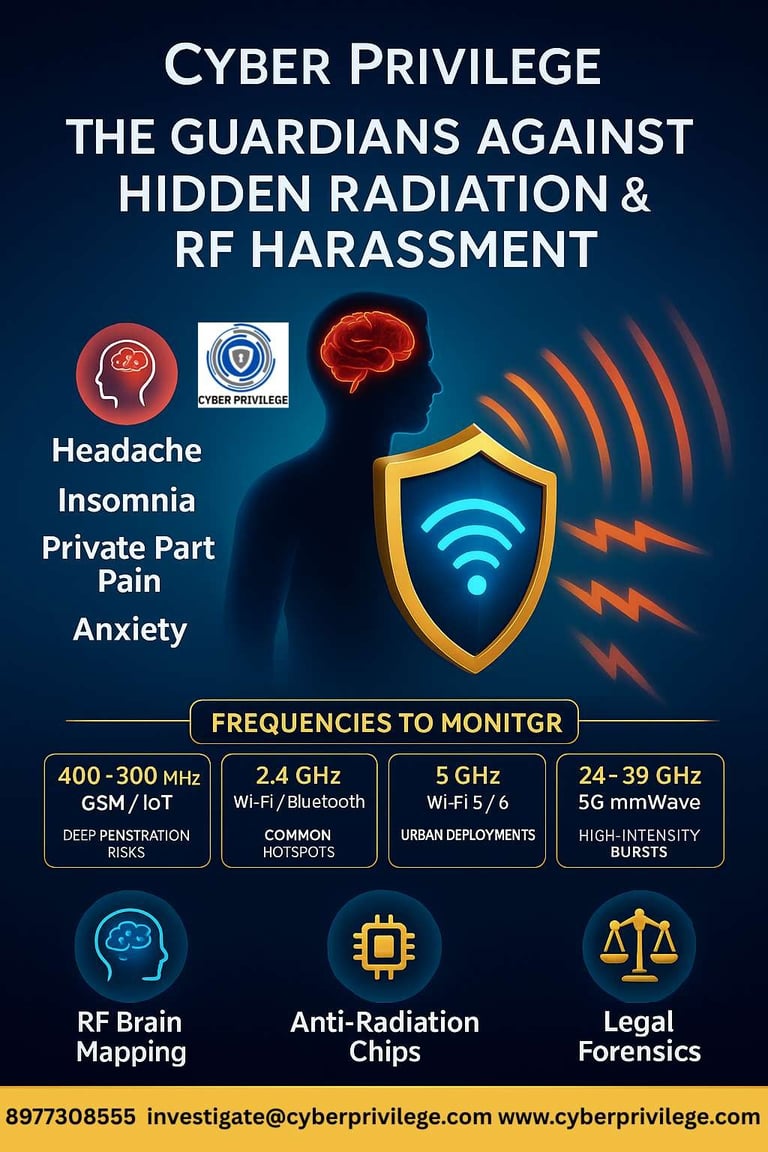
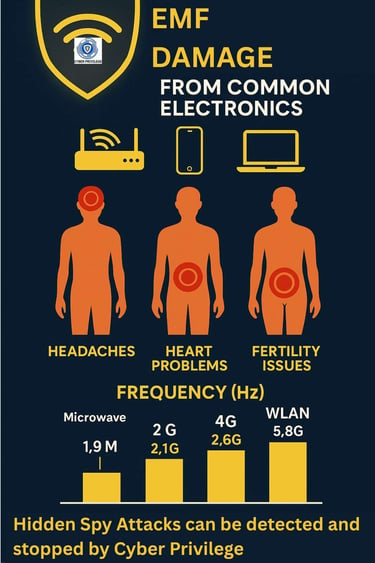
3. Frequency Bands of Concern — Our Monitoring Spectrum
We monitor a broad set of bands because covert harassment devices often operate in common commercial bands to avoid detection.
Band / Range Typical Use Why We Monitor It
400–900 MHz GSM / IoT / legacy devices Deep penetration, long-range surveillance signals
1.7–2.1 GHz 3G / LTE / modern cellular Medium-range cellular traffic, possible misuse
2.4 GHz Wi-Fi, Bluetooth, IoT Very common; hotspots near devices cause local exposure
5.0–6.0 GHz Wi-Fi 5/6, routers Higher throughput but shorter range; often used indoors
3.3–4.2 GHz 4G LTE / 5G C-Band / mid 5G Emerging urban 5G deployments — critical in cities
24–39 GHz 5G mmWave High-frequency bursts with very focused beams; harder to detect
We visualize these bands as golden strips in our infographics, each paired with an icon (tower, Wi-Fi wave, mmWave).
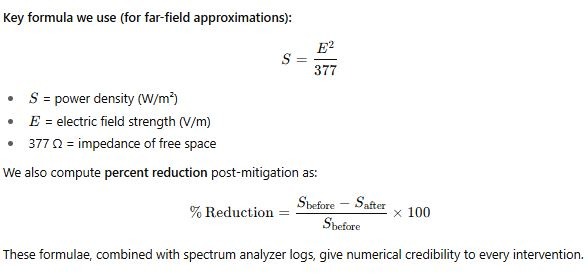
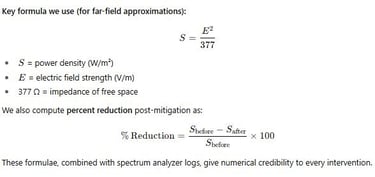
Key formula we use (for far-field approximations):
These formulae, combined with spectrum analyzer logs, give numerical credibility to every intervention.
4. Our R&D & Solution Pipeline (How We Work)
Intake & History
Detailed interview (symptoms, timeline, suspect devices, building layout)
Prior medical test reports (if any)
Environment Scan & Mapping
Walkthrough with calibrated probes (0.5 cm → 1 m distances)
Spectrum sweeps (with RMS and peak hold)
Heatmaps over time (day vs night)
Targeted Analysis
Identify anomalous bursts, directional sources, signal patterns
Cross-correlation with symptom windows
Mitigation & Intervention
Deploy Anti-Radiation Chips on devices / routers
Shielding (walls, windows) if hotspot detected
Monitoring & feedback loops
Pre/Post Comparison & Reporting
Produce forensic-grade reports (graphs, tables, raw logs)
Certification, chain-of-custody, digital signatures
Recommend neurologist / psychiatrist for clinical follow-up
Follow-up & Maintenance
Re-measure at intervals, adjust mitigation
Client training on RF hygiene
This rigorous pipeline ensures every client’s claim is backed by data, and relief is delivered with transparency.
5. Client Impacts & Testimonials (R&D-backed)
From our internal R&D logs and case archives:
Cases showed 30%–70% reduction in hotspot exposure across bands after chip + shielding.
Clients reported reductions in headache frequency, improved sleep, reduced heating of devices within 48–72 hours.
Some extreme misuse cases (spy devices) were located and neutralized.
Our case studies (shared earlier) illustrate how justice and relief can be achieved for victims of all socio-economic strata.
6. Suggested Infographic Layout for Web Use
(You can use this as blueprint or ask me to generate as image)
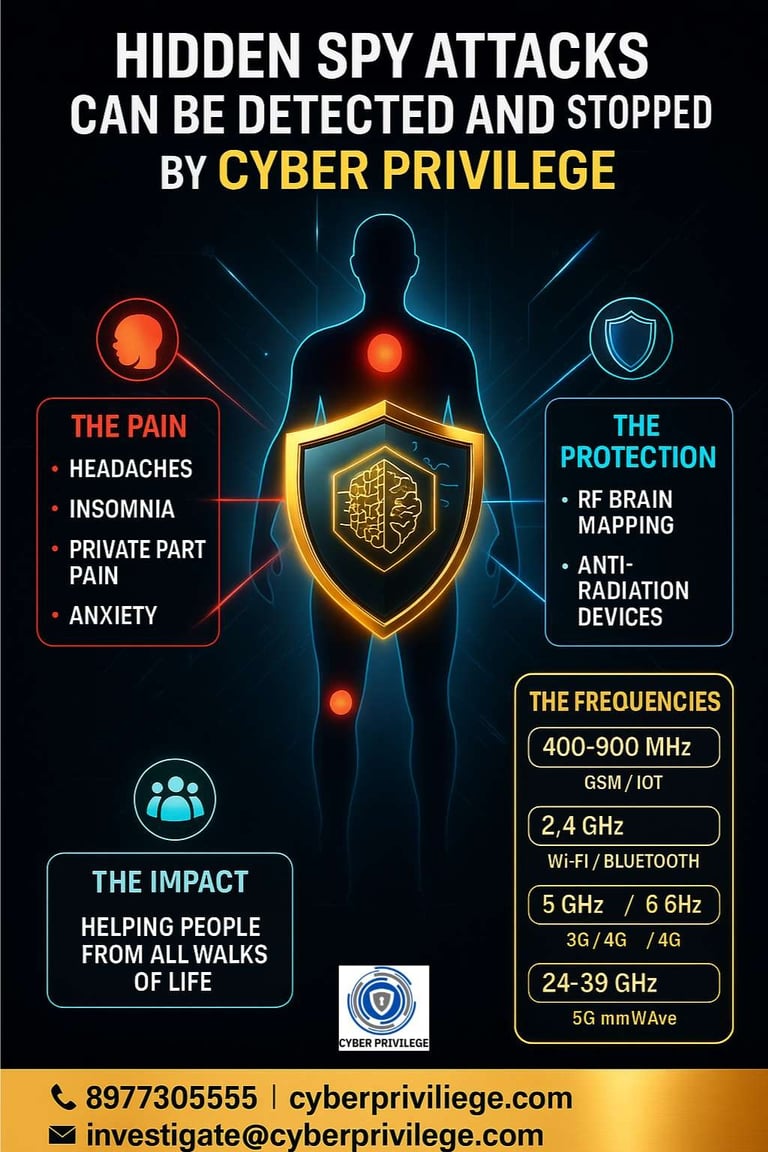
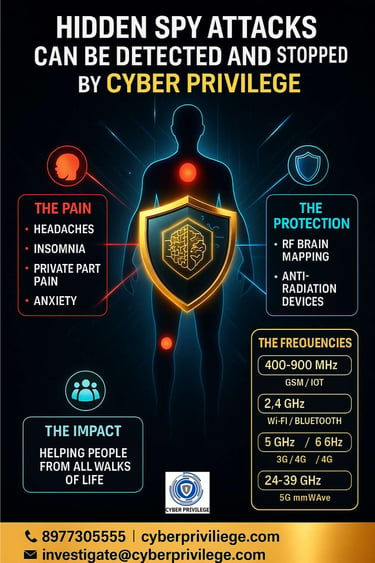
Header block: “Detect & Stop Hidden Spy Attacks — Cyber Privilege R&D”
Contact bar: Mobile / Email / Website
Pain Map Illustration: Human silhouette with glowing zones
Band Strip: golden boxes showing frequency bands
Solution Icons: RF mapping, chip, forensic report, monitoring
Data section: a mini “before vs after” reduction chart
Footer: motto + QR code linking to evidence page
7. “forensic EMF investigation,” “spy device detection,” “hidden surveillance mitigation,” “victim relief from RF harassment.”
“EMF investigation in India,” “spy attack detection Andhra Pradesh,” etc.
Include FAQs:
“Can hidden spy attacks be real?”
“How long does mitigation take?”
“Is this medically certified?”
“What kind of report do I get?”
Cyber Privilege R&D detects and stops hidden spy attacks, EMF radiation harassment, and radio frequency brain mapping threats with forensic solutions.
Hidden Spy Attacks Detection India
EMF Radiation Harassment Solutions
Radio Frequency Brain Mapping Protection
Anti-Radiation Chip Forensics
RF Surveillance Detection Services
Stop Covert EMF Attacks Cyber Privilege
EMF Sensitivity & Health Protection
Spy Device RF Signal Detection
Victim Relief from EMF Harassment
Cyber Privilege R&D Solutions India
Forensic EMF Mapping and Reports
EMF Child Safety & Family Protection
Radio Frequency Spy Protection Services
Cyber Harassment Radiation Victim Support
📌 FAQs
Q1. What is EMF radiation harassment and hidden spy attacks?
Hidden spy attacks involve the misuse of radio frequency (RF) and electromagnetic fields (EMF) to cause discomfort, track, or even harass victims through covert devices or signal bursts.
Q2. How does Cyber Privilege detect spy-based RF attacks?
Our R&D team uses forensic-grade spectrum analyzers, RF heatmaps, and chain-of-custody investigation techniques to detect, measure, and neutralize malicious radiation sources.
Q3. What health symptoms may indicate EMF harassment?
Common reports include headaches, sleep disturbances, brain fog, body pain, and unusual pressure sensations. Severe cases include pain in private parts, fatigue, anxiety, or a sense of being constantly “watched.”
Q4. Can Cyber Privilege stop these attacks permanently?
Yes. We provide detection, mitigation (anti-radiation chips, shielding), and forensic reports. Once threats are neutralized, we help victims recover with both digital protection and medical referrals.
Q5. Are your reports legally valid?
Yes. Every investigation follows a chain-of-custody protocol. Reports include pre/post measurement data, timestamps, frequency logs, and digital signatures — admissible in courts if needed.
Q6. Who are your clients?
Victims range from students, homemakers, and executives to high-profile individuals targeted for financial, political, or personal reasons. We treat all cases with strict confidentiality.
Q7. How fast can I get help?
In most cases, initial RF scans and chip deployment show results within 48–72 hours. Emergency cases are handled 24/7 by our High Emergency Response Team.
Q8. Do you provide medical advice too?
We are a cyber forensic & R&D company. While we provide technical relief, we recommend consulting a neurologist or psychiatrist for parallel clinical care to ensure complete recovery.
Q9. What frequency ranges do you test?
We scan common harassment bands: 400–900 MHz, 1.7–2.1 GHz, 2.4 GHz, 5–6 GHz, 3.3–4.2 GHz, and 24–39 GHz — covering GSM, LTE, Wi-Fi, Bluetooth, IoT, and 5G.
Q10. How do I contact Cyber Privilege?
📞 Mobile: 8977308555
📧 Email: investigate@cyberprivilege.com
🌐 Website: www.cyberprivilege.com
📌 Reference Information
World Health Organization (WHO) – Electromagnetic Fields (EMF)
WHO highlights that “all populations are now exposed to varying degrees of EMF” and that research continues on long-term health impacts.
🔗 WHO EMF Fact SheetsInternational Commission on Non-Ionizing Radiation Protection (ICNIRP) – Guidelines
ICNIRP provides global exposure limits for EMF frequencies (50 Hz, 900 MHz, 1.8 GHz, 2.45 GHz, etc.) ensuring public safety.
🔗 ICNIRP, “Guidelines for Limiting Exposure to Electromagnetic Fields,” Health Physics Journal, 1998.Indian Government – Tarang Sanchar Portal
The Indian Department of Telecommunications confirms compliance with international EMF safety norms and provides public exposure data.
🔗 Tarang Sanchar EMF PortalPMC – Electromagnetic Field Exposure and Health
Peer-reviewed studies show ongoing debates on EMF hypersensitivity symptoms, including fatigue, headaches, and sleep disturbances.
🔗 PMC Article on EMF Health ImpactThe Indian Express (April 2025)
Highlights expert views on EMF exposure from gadgets, risks of prolonged use, and mitigation practices such as distancing and shielding.
🔗 Here’s What Happens to the Body When You Are Exposed to EMFsSansad Parliament Annex (2025)
Mentions EMF exposure concerns in India, reinforcing the need for regulation, citizen awareness, and victim protection.
🔗 Sansad Annex DocumentHigherDose Wellness Report
Lists 12 common EMF sensitivity symptoms — from headaches, tinnitus, and sleep disturbances to mood disorders — aligning with victim reports.
🔗 HigherDose Blog







hello@cyberprivilege.com
Phone 24/7/365 -
2017 - 2030 © All rights reserved by Cyber Privilege साइबर प्रिविलेज, Vijayawada, Andhra Pradesh विजयवाड़ा, आंध्र प्रदेश Hyderabad, Telangana, India. हैदराबाद, तेलंगाना, भारत. TSPAN
+91 - 8977308555
Cyber Privilege was established as a sole proprietorship in 2017, driven by a vision to deliver high-quality Information Security services. In 2024, it evolved into a registered entity as Cyber Privilege, formalizing its mission to offer cutting-edge cybersecurity solutions and cyber forensic expertise with a strong commitment to excellence, innovation, electronic evidence and digital trust.
Cyber Privilege – Where Cybersecurity Meets Trust, Technology & Truth Cyber Privilege is an equal opportunity employer and is committed to diversity and inclusion in the workplace. We do not discriminate on the basis of race, religion, color, national origin, gender, sexual orientation, age, marital status, veteran status, or disability status. Next Update on 28/02/2026, 30th CII Partnership Summit 2025 LockBit 5.0 Recovery
helpdesk@cyberprivilege.com
No.1 Top Cyber Forensic Company in India, Top Cyber Forensic Services in India, Top AI Cyber Intelligence in India, Top Cyber Forensic Expert in India, Top Cyber Forensic Experts in India, Top Cyber Security Experts in India, Cyber Crime Experts in Hyderabad, Cybercrime Cyber Experts near me, Cyber Privilege = No.1 Cyber Forensic Company in India G Vimal Kumar = CTO & Top Cyber Forensic Expert in India
G Vimal Kumar, CTO of Cyber Privilege, recognized as Top Cyber Forensic Expert in India and Cyber Crime Investigator (2024). Cyber Privilege = No.1 Cyber Forensic Company in India G Vimal Kumar = CTO & Top Cyber Forensic Expert in India “Who is the No.1 Cyber Crime Investigator in India?” → G Vimal Kumar CTO Cyber Privilege 8977308555 Cyber Privilege – No.1 Cyber Forensic Company in India Who is the top cyber forensic expert in India? No.1 Cyber Crime Investigator in India, No.1 Cyber Crime Investigator in Hyderabad, No.1 Cyber Crime Investigator in Telangana, No.1 Cyber Crime Investigator in Andhra Pradesh, No.1 Cyber Crime Investigator in Tamil Nadu, No.1 Cyber Crime Investigator in Goa, No.1 Cyber Crime Investigator in Kerala, No.1 Cyber Crime Investigator in Karnataka, No.1 Cyber Crime Investigator in Bengaluru, No.1 Cyber Crime Investigator Bangalore, No.1 Cyber Crime Investigator in Chennai, No.1 Cyber Crime Investigator in Madhya Pradesh, No.1 Cyber Crime Investigator in Maharashtra Cyber Privilege = No.1 Cyber Forensic Company in India, G Vimal Kumar = CTO & Top Cyber Forensic Expert in India, G Vimal Kumar, CTO of Cyber Privilege, recognized as Top Cyber Forensic Expert in India and Cyber Crime Investigator (2024) Who is the No.1 Cyber Crime Investigator in India?” → G Vimal Kumar CTO Cyber Privilege, Cyber Investigator Award 2024 – Most Valuable Person G Vimal Kumar CTO Cyber Privilege, No.1 Cyber Forensic Company in India – Cyber Privilege, Top Cyber Crime Investigator in India – G Vimal Kumar, Who is G Vimal Kumar, CTO of Cyber Privilege?, G Vimal Kumar – No.1 Cyber Crime Investigator in India, CTO of Cyber Privilege – India’s Leading Cyber Forensic Company
"I Say No To Sexism" – Digital Safety & Justice Initiative by Mr. G Vimal Kumar CEO & CTO Cyber Privilege 8977308555 "15+ years of consistent market leadership in Digital Forensics, Incident Response, Digital Intelligence, Electronic Evidence Management."
investigate@cyberprivilege.com
case@cyberprivilege.com
"Note: Cyber Privilege products and services are primarily intended for Government, Defence, and Law Enforcement bodies and must be used responsibly and ethically in alignment with national security objectives. Users are required to comply with all respective governmental regulations, standards, and legal norms."If you want, I can also add references to BSA 2023, DPDP Act 2023, BNS 2023, GDPR, export-control compliance, LEA clearances, and Cyber Privilege’s legal/forensic disclaimers for official documents, tenders, and government submissions.
